Satish Kumar Perumal
Unified Security
The Unified Security project transformed Netscaler’s security suite from a consultant-dependent nightmare into a streamlined, self-service platform. This wasn’t a UI facelift—it was a fundamental rethinking of how enterprise customers configure and monitor application security.
Role
Lead Product Designer
Timeline
4.5 months
Led end-to-end redesign of Citrix’s security configuration and analytics system, integrating ML-powered intelligence while coordinating 31 stakeholders across engineering, product, and leadership teams.

Customers were hemorrhaging money on external consultants or abandoning our security suite entirely
Despite having industry-leading WAF, bot detection, and DDoS protection, our configuration process was so convoluted that experienced admins needed consultant support.
The Problems: Security Configurations: A Revenue leak
The Cost? Customers either,
Hired expensive consultants
Switched to competitors with simpler interfaces
Ignored security features altogether, leaving apps vulnerable
Evaluating existing experience
Security Configurations
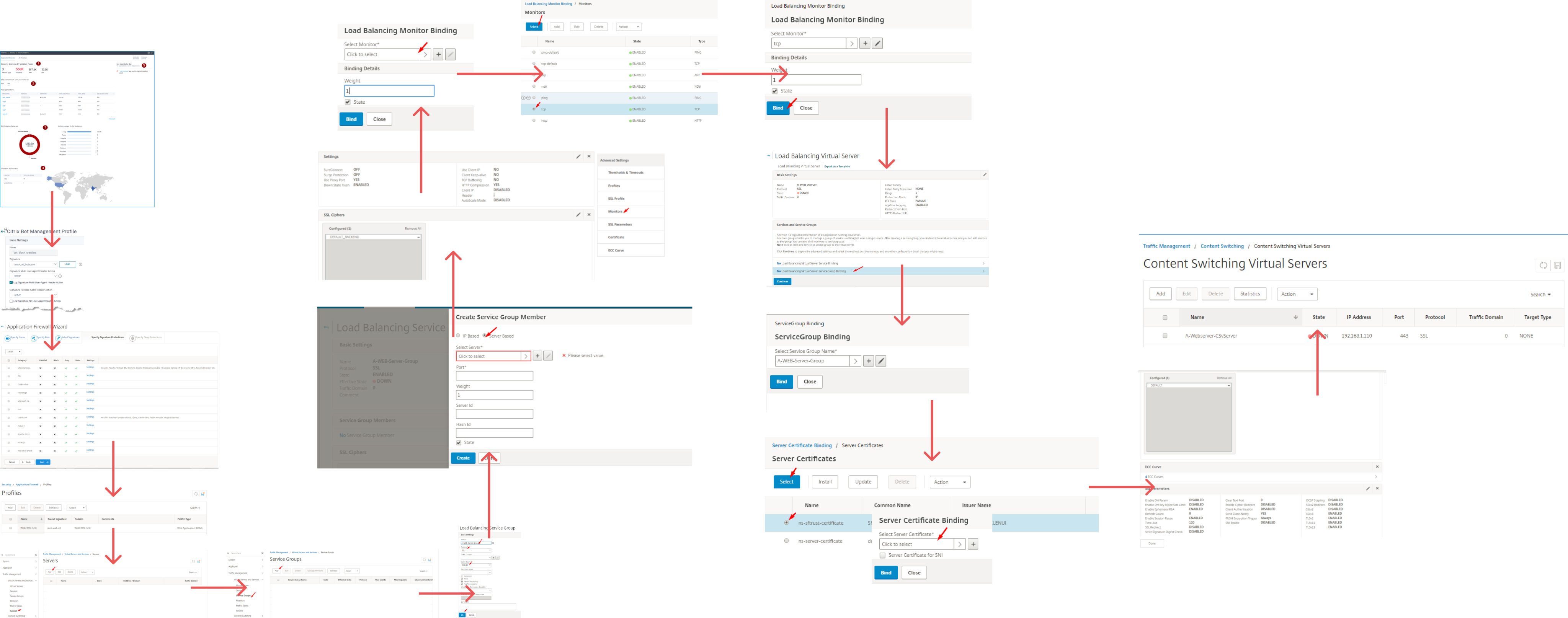
Configuring bot protection for a single application required navigating 15+ screens across 6 different modules. The workflow diagram below wasn’t documentation—it was the actual torture path users had to navigate.
Every application needed:
- Signature file creation
- Policy binding (multiple layers)
- Profile configuration
- Rate limiting setup
- Action specification
- Log aggregation mapping
This repeated for WAF, DoS, and advanced threat protection. Multiply that by 50–100 applications per enterprise customer. You see the problem.
Security Analytics
Telemetry showed <5% user engagement. Not because customers didn’t need security insights—they desperately did. But our dashboard was a data dump, not a decision tool.
What users faced:
- Fragmented metrics across disconnected views
- No correlation between threat types and affected applications
- No actionable intelligence (just numbers without context)
- Navigation required deep product knowledge to find anything useful
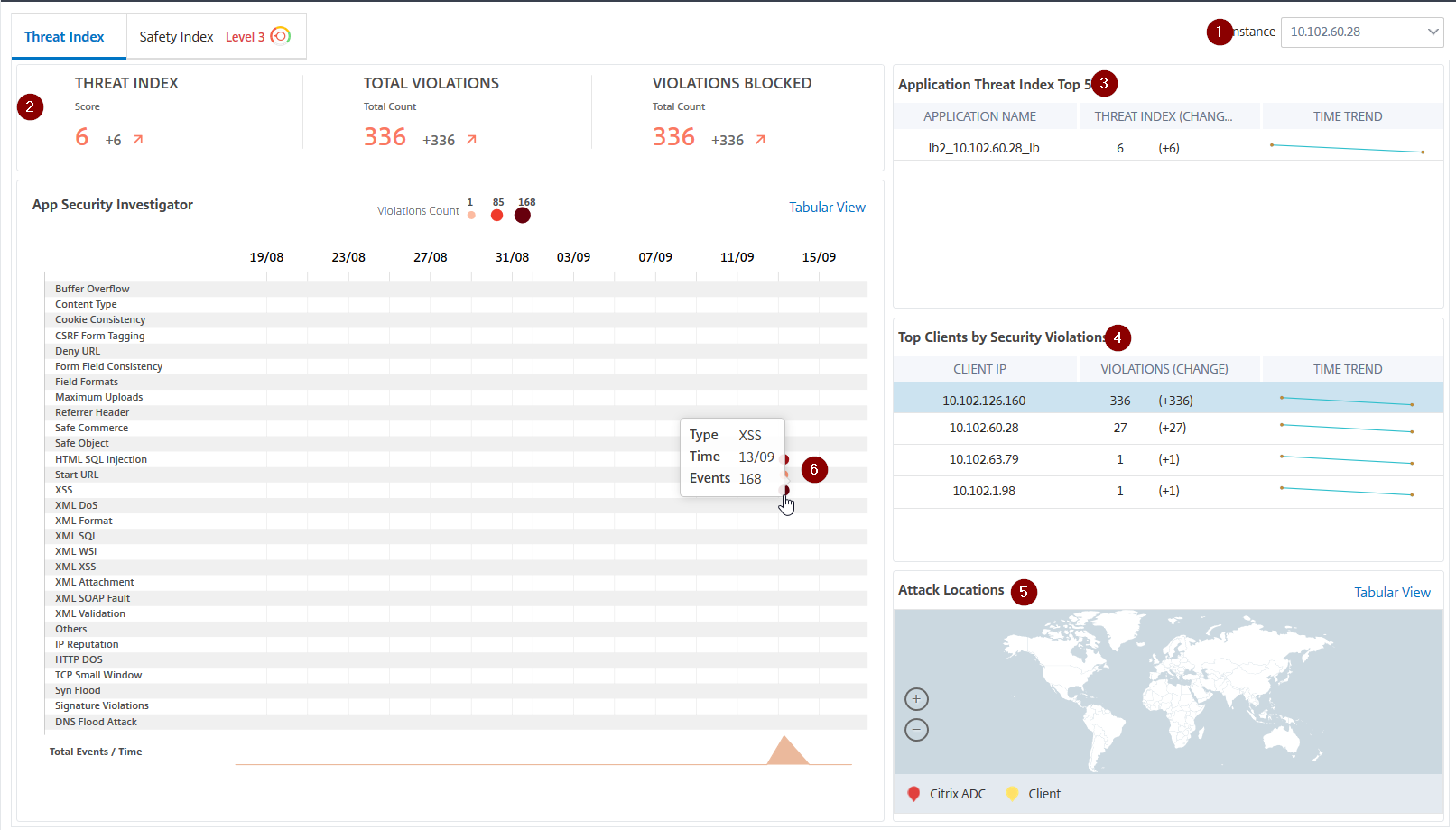
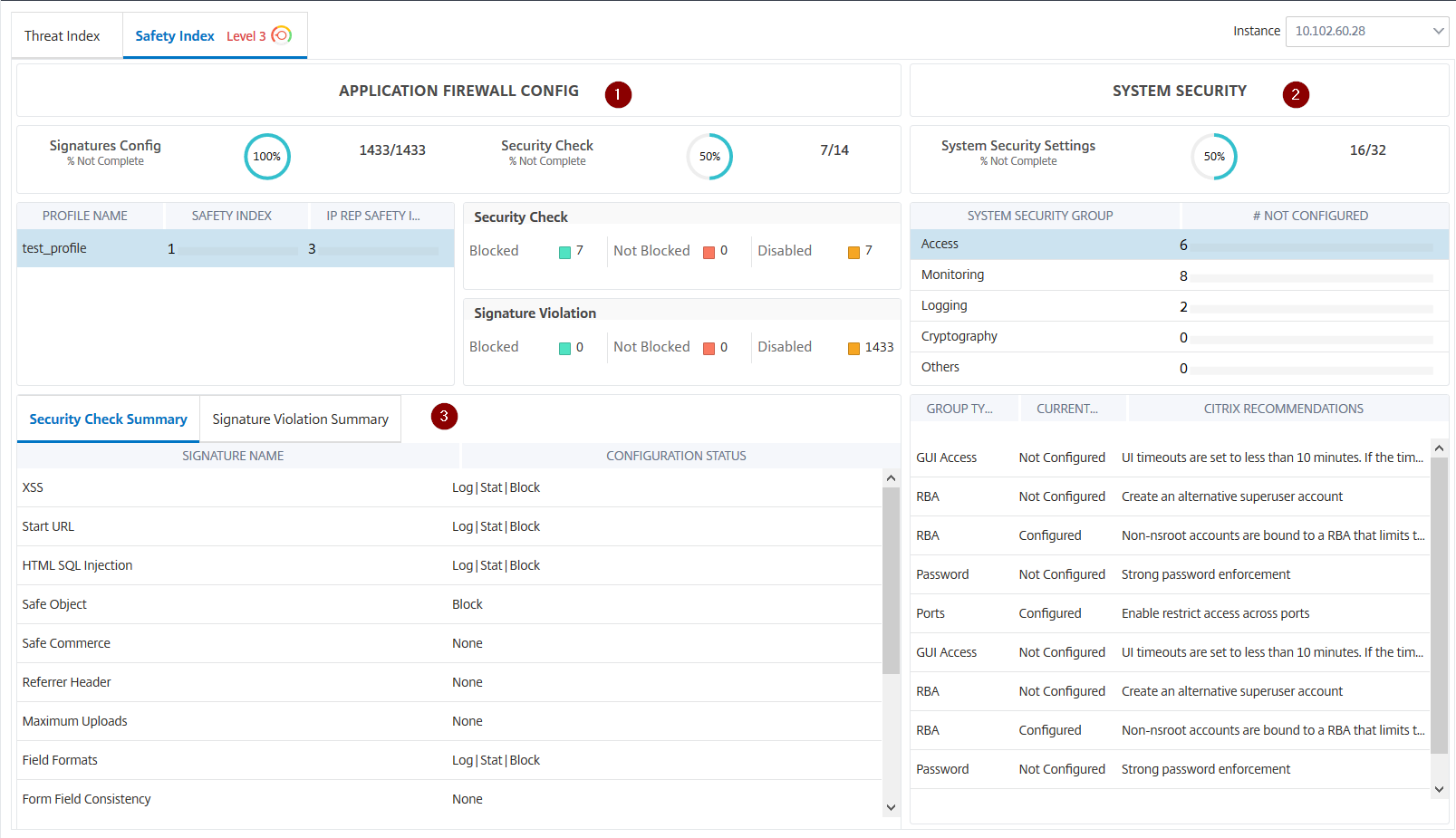
So, the real problem:
Security admins needed answers to questions like “Which applications are under attack right now?” and “What’s the business impact of this DDoS spike?” Our dashboard made them work for it. Competitors handed them the answer.
/satish-kumar-perumal
Email ID
satishkumar@gmail.com
Mobile
(+91) 9901094145
Interested in the full case study?
Due to client confidentiality, I share detailed workflows, research findings, and implementation insights
in direct conversations.